Shadow IT and the New Prometheus
/This blog post is sponsored by the Enterprise CIO Forum and HP.
Over twenty-five years ago, business-enabling information technology was still in its nascent phase. The Internet was still coming of age and the World Wide Web didn’t exist yet. The personal computer revolution had only recently started and it was still far from going mainstream. And the few mobile phones that existed back then were simply phones—not mini-supercomputers.
Back in those dark ages, most organizations had a centralized IT department, which selected, implemented, and controlled the technology used to support business activities. Since information technology was a brave new world and the organization was so dependent on its magic (Clarke’s Third Law: “Any sufficiently advanced technology is indistinguishable from magic.”), the IT department was allowed to dictate that everyone used the same type of computer, loaded with the same standard applications, which provided, for the most part, the same general information technology solution for a myriad of business problems.
Shadow IT was the term used to describe business-driven information technology solutions not under the jurisdiction of IT, and thus operated in the shadows by business users who had to carefully conceal their use of non-IT-sanctioned technology.
Returning to the light of the present day, it’s difficult to imagine life—both personal and professional—without the Internet and the World Wide Web, personal computers, and the growing prevalence of smart phones, tablet PCs, and other mobile devices.
In Greek mythology, Prometheus stole fire from the gods and gave it to us mere mortals. And once humans could command fire, we combined it with our use of other enabling tools, thus learning that we were capable of taking control of our own destiny.
The consumer-driven trends of cloud computing, SaaS, and mobility are the New Prometheus stealing the fire of technology from the IT department and giving it directly to business users, thus enabling them to take control of their own IT destiny.
The consumerization of IT has demystified business-enabling information technology. The fire stolen by the New Prometheus is allowing business-driven, business-function-specific, and decentralized IT solutions to finally step out of the shadows.
Although IT Delivery remains a strategic discipline for the organization, the tactical and operational execution of that strategy needs to be decentralized and embedded within the business functions of the organization. Communication and collaboration are more important than ever, but the centralization and generalization of information technology is a thing of the past.
This blog post is sponsored by the Enterprise CIO Forum and HP.
Related Posts
The Good, the Bad, and the Secure
Securing your Digital Fortress
Are Cloud Providers the Bounty Hunters of IT?
The Diderot Effect of New Technology
The IT Consumerization Conundrum
The IT Prime Directive of Business First Contact
A Sadie Hawkins Dance of Business Transformation
Are Applications the La Brea Tar Pits for Data?
Why does the sun never set on legacy applications?
The IT Pendulum and the Federated Future of IT

 Abraham Maslow’s Hierarchy of Needs
Abraham Maslow’s Hierarchy of Needs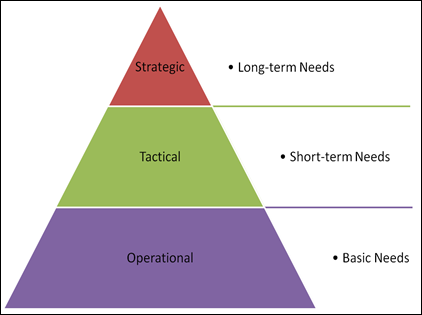 Information Technology’s Hierarchy of Needs
Information Technology’s Hierarchy of Needs
